Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is one of the least secure forms of security. A network that is secured with WEP has been cracked in 3 minutes by the FBI. WEP is an old IEEE 802.11 standard from 1999 which was outdated in 2003 by WPA or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device which encrypts the network with a 256 bit key; the longer key length improves security over WEP.
Wireless security is used to limit the scope of users that have access to services you install when implementing a wireless access point or wireless router device. These devices are used to provide convenient intranet and/or Internet access without having to run cable through buildings or other areas of coverage where return on investment is low. There are two methods used with wireless systems today to limit access:
- Coverage Area
- Authentication and Authorization Mechanisms
Coverage Area
You can limit coverage area with an access point by using the proper antenna for the coverage needs. This prevents our wireless signals from emitting beyond your coverage area. Unfortunately, with the proper antenna in place on the receiver side, this method is easily defeated. An individual or group who has enough interest and funding to buy better equipment is the limiting factor here.
Authentication and Authorization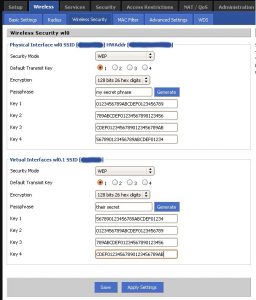
You can also limit access to services by having proper authentication and authorization services in place that are required before wireless system access is permitted. This requires configuration of authentication services on your wireless devices which should include encryption in the transport.
Disabling SSID Broadcast
Some devices allow you to disable “SSID Broadcast”. Although this helps to limit who might see which networks are available to attack, knowledgeable attackers do not rely on SSID values to attack systems. SSID values can also be determined if an attacker is using a network sniffer with wireless capabilities. Disabling SSID broadcast also makes it more difficult for the intended users of the wireless network to configure and connect to the wireless network. This is considered to be a “security through obscurity” technique.
Picking an Encryption Technology
There are a few common encryption technologies used in wireless infrastructures today.
WEP or Wired Equivalent Privacy
WEP is usually found in 64bit, 128bit, and 256bit implementations. WEP has been found to be weak cryptographically, and should not be used for any wireless infrastructure you would like to have secured. Choosing a good passphrase or password does not increase the level of security offered by WEP.
WPA – Wifi Protected Access
WPA is based on WEP, but the WPA algorithm changes the effective key more often. WPA is still weak cryptographically, so choosing a passphrase or password of 20 characters or more is important to keep your wireless network secure. If you use a good passphrase with WPA is it believed that attacks are impractical?
WPA2 – the Second Generation of Wifi Protected Access
WPA2 uses new encryption technologies called AES or TKIP which are not based on WEP. WPA2 is the preferred encryption technology if it is available. As of March 13, 2006, all equipment using the WiFi trademark must be certified for WPA2.
Mixing WPA and WPA2 clients
Devices that support WPA2 mixed mode allow clients using both AES and WEP configurations to interoperate. This does not include broadcast and multicast traffic.
Encryption Keys
Encryption requires a key exchange for the algorithms to have a common starting point. Wireless devices usually provide two methods for key exchange, pre-shared keys (PSK or password), and enterprise (RADIUS). For individuals and small businesses it is better to use a pre-shared key mechanism. For environments it will have many different wireless access devices, enterprise is generally a better choice.
- Pre-shared keys – A pre-shared key is just a password or passphrase you configure on all of your wireless devices and clients so they can initiate communication. Selecting a good password is imperative in providing the proper level of security for your wireless network.
- Enterprise – Enterprise key exchange is usually provided by a RADIUS service. Both systems connect to the RADIUS system for the initial key exchange. This method makes it easier to manage more wireless devices and clients with less effort.
Authentication and Authorization can be provided by many means including:
- MAC address filters
- Login and Password credentials validation
- Identity validation through public key encryption, soft-token, or certificates
- Identity validation through hard-token or key FOB
MAC Address Filters
MAC address filtering prevents or allows clients to attach to your wireless network using a look-up table. If the wireless network card MAC address is on the list it can be permitted or allowed. Unfortunately, a knowledgeable attacker can use a wireless network sniffer to capture MAC address values of currently connected systems and change his MAC address value accordingly. It is a trivial matter to change your systems MAC address. Because of this, this security technique is considered “security through obscurity.”
Login and Passwords
Some systems will not pass traffic from connected systems until the user authenticates with the wireless device. The authentication details may be stored in a table locally on the wireless device, or they may be checked remotely from the device using the RADIUS protocol, TACACS, or some other remote authentication technology.
Soft-tokens and Certificates
Soft-tokens is a software package installed on client systems that interact with the authentication and authorization software on the wireless device to validate users.
Certificates are special files installed on the client machine that must properly match up with certificate information on the wireless device to validate a wireless network client.
Hard-tokens and Fobs
Hard-tokens are small computing devices that use a challenge-response mechanism with the wireless device to validate a user or wireless network client.
A Fob is a piece of hardware you can attach and detach from a client system that provides credentials to the wireless device for client validation.
To sum up, you should use WPA2, then WPA, and then WEP in that order, for your wireless encryption if you have a choice. Setting up WEP is better than having a completely open wireless network. For key exchange use pre-shared keys if you don’t many wireless devices to manage, or set up a RADIUS server for that function if you have lots of devices to manage. You can disable SSID Broadcast, and use MAC filtering, but don’t rely on them solely to secure your wireless network.
More Related Wireless Topics:
Simple Ways to Secure Wireless Network
How to Set up WEP, WPA or WPA2 Personal Wireless Security on a Linksys Wireless Router?