In computer networking, network address translation (NAT) is the process of modifying IP address information in IP packet headers while in transit across a traffic routing device.
Here we will focus on NAT and PAT, as well as the related access control list changes. This only addresses typical static and dynamic source address translation scenarios. Policy based NAT and DMZ configuration will be address in future articles. This is an area of significant change in ASA 8.4.
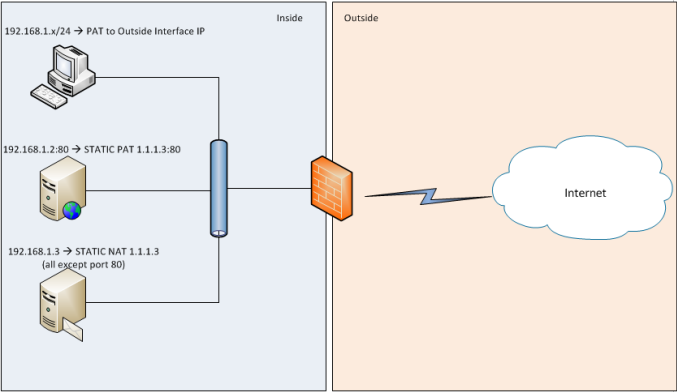
For this configuration challenge, we will meet following configuration requirements:
- 192.168.1.x/24 should use the outside interface IP for Dynamic PAT
- 192.168.1.2 TCP Port 80 will have a static PAT translation to 1.1.1.3 Port 80
- 192.168.1.3 will have a static NAT (one-to-one) translation to 1.1.1.3
Note: The last two requirements overlap. The desire is that only traffic to TCP port 80 on 1.1.1.3 be delivered to 192.168.1.2. All other traffic coming in to 1.1.1.3 will go to 192.168.1.3.
For those familiar with ASA version 8.2 and earlier, the relevant configuration excerpts are found below.
nat (inside) 1 0.0.0.0 0.0.0.0
global (outside) 1 interface
static (inside,outside) tcp 1.1.1.3 www 192.168.1.2 www netmask 255.255.255.255
static (inside,outside) 1.1.1.3 192.168.1.3 netmask 255.255.255.255
//ACL Entries–Note the translated addresses
access-list outside_access_in extended permit tcp any host 1.1.1.3 eq www
access-list outside_access_in extended permit tcp any host 1.1.1.3 eq smtp
access-list outside_access_in extended permit tcp any host 1.1.1.3 eq https
access-list outside_access_in extended permit icmp any host 1.1.1.3access-group outside_access_in in interface outside
If you reproduce this configuration, it is imperative that the static translations be entered in the exact order. By doing so, the static NAT configuration is implemented with the exception of the the previously entered static PAT entry.
ciscoasa(config)# static (inside,outside) tcp 1.1.1.3 80 192.168.1.2 80
ciscoasa(config)# static (inside,outside) 1.1.1.3 192.168.1.3
WARNING: mapped-address conflict with existing static
TCP inside:192.168.1.2/80 to outside:1.1.1.3/80 netmask 255.255.255.255
Comparing NAT and access-list configuration to the 8.4 equivalent, major changes are apparent. After performing an upgrade of the 8.2 configuration, the following is an excerpt that represents the 8.4 NAT and ACL configuration.
//object definitions
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network obj-192.168.1.2
host 192.168.1.2
object network obj-192.168.1.3
host 192.168.1.3
//NAT Assignments
object network obj_any
nat (inside,outside) dynamic interface
object network obj-192.168.1.2
nat (inside,outside) static 1.1.1.3 service tcp www www
object network obj-192.168.1.3
nat (inside,outside) static 1.1.1.3
//ACL Interface Binding
access-group outside_access_in in interface outside
//ACL Entries–Note the real IP address
access-list outside_access_in extended permit tcp any host 192.168.1.2 eq www
access-list outside_access_in extended permit tcp any host 192.168.1.3 eq smtp
access-list outside_access_in extended permit tcp any host 192.168.1.3 eq https
access-list outside_access_in extended permit icmp any host 192.168.1.3
As you can quickly see ASA 8.4 radically changes the NAT configuration. A good way to get a grasp of the differences is to go through the upgrade process between 8.2 and 8.4 with known working configurations.
Best Cisco ASA Guide Book: Cisco ASA: All-in-One Firewall, IPS, Anti-X, and VPN Adaptive Security Appliance (2nd Edition)
Book Des: For organizations of all sizes, the Cisco ASA product family offers powerful new tools for maximizing network security. Cisco ASA: All-in-One Firewall, IPS, Anti-X and VPN Adaptive Security Appliance, Second Edition, is Cisco’s authoritative practitioner’s guide to planning, deploying, managing, and troubleshooting security with Cisco ASA. Written by two leading Cisco security experts, this book presents each Cisco ASA solution in depth, offering comprehensive sample configurations, proven troubleshooting methodologies, and debugging examples. Readers will learn about the Cisco ASA Firewall solution and capabilities; secure configuration and troubleshooting of site-to-site and remote access VPNs; Intrusion Prevention System features built into Cisco ASA’s Advanced Inspection and Prevention Security Services Module (AIP-SSM); and Anti-X features in the ASA Content Security and Control Security Services Module (CSC-SSM). This new edition has been updated with detailed information on the latest ASA models and features.
- Everything network professionals need to know to identify, mitigate, and respond to network attacks with Cisco ASA
- Includes detailed configuration examples, with screenshots and command line references
- Covers the ASA 8.2 release
- Presents complete troubleshooting methodologies and architectural references
More Reviews on Cisco ASA book you can visit amazon.com see more details…
More Cisco CCIE Tips:
Cisco ASA 8.3, 8.4 Hairpinning NAT Configuration
How to Upgrade a Basic ASA Configuration to 8.4?
Simple Steps to Connect a Remote Office to Cisco ASA 5510
How to Configure Cisco ASA 5505 Firewall?
VLAN Sub-Interfaces on Cisco ASA 5500 Firewall Configuration