Here we go, with the configuration of DHCP snooping on a Cisco Switch. This feature protects the network by allowing the Cisco Switches to accept DHCP response message only from the authorized servers connected to the trusted interfaces in a Cisco Switch.
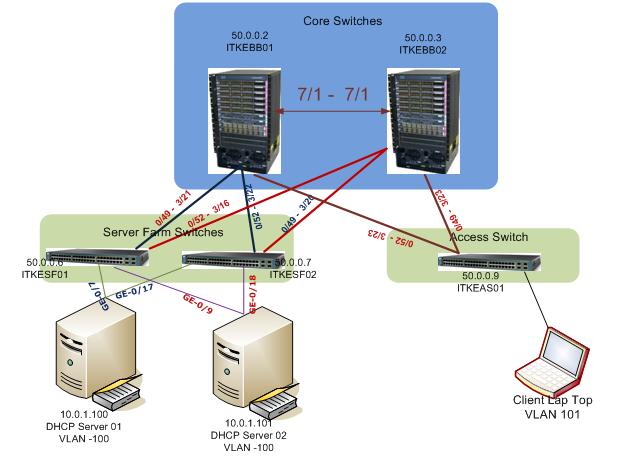
All Switch to Switch connections are configured as 802.1 1Q Trunk ports.
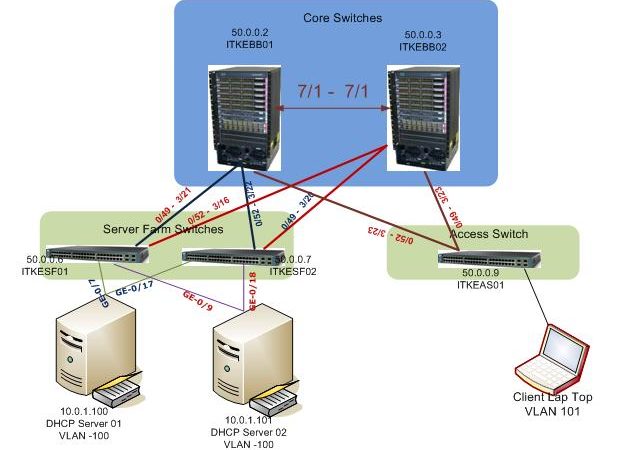
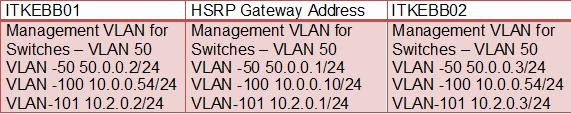
IP Address and HSRP Details for the Core Switches
From the above scenario we have two Cisco 6513 Series Switches as a Core/ Distribution with three VLANS one for management of Switches VLAN 50,VLAN 100 for all the servers and VLAN 101 for clients. Two Cisco 3560 Series Switches as Server Farm Switches and a Cisco 3560 Series Switch as an Access Switch. There are two DHCP servers with an IP address 10.0.1.100 and 10.0.1.101 connected with Server Farm Switches with HP NIC teaming. We configure DHCP Snooping based on above scenario.
The first step to configure DHCP Snooping is to turn on DHCP snooping in all Cisco Switches using the “ip dhcp snooping” command.
All Cisco Switches (config)#ip dhcp snooping Second step is to configure the trusted interfaces, from the above scenario all trunk ports are configured as trusted ports as well as the interfaces G0/7,(ITKESF01 50.0.0.6), G0/17,(ITKESF02 50.0.0.7), G0/9 ITKESF01 50.0.0.6) and G0/18 ITKESF02 50.0.0.7) connected to DHCP servers with IP 10.0.1.100 and 10.0.1.101. Let’s configure all trunk ports in ITKEBB01
ITKEBB01(config)#interface range gigabitEthernet 3/21 – 23
ITKEBB01 (config-if)#ip dhcp snooping trust
Now let’s configure all trunk ports in ITKEBB02
ITKEBB02(config)#interface range gigabitEthernet 3/21 – 23 ITKEBB02 (config-if)#ip dhcp snooping trust
ITKEBB02 (config)#interface gigabitEthernet 3/16
ITKEBB02 (config-if)#ip dhcp snooping trust
Now let’s configure the trusted ports for the DHCP servers
ITKESF01(config)#interface gigabitEthernet 0/7
ITKESF01 (config-if)#ip dhcp snooping trust
ITKESF01(config)#interface gigabitEthernet 0/17 ITKESF01 (config-if)#ip dhcp snooping trust
ITKESF02(config)#interface gigabitEthernet 0/9
ITKESF02 (config-if)#ip dhcp snooping trust
ITKESF02(config)#interface gigabitEthernet 0/18 ITKESF02 (config-if)#ip dhcp snooping trust
Now let’s configure the trunk ports Access Switch ITKEAS01
ITKEAS01(config)#interface range gigabitEthernet 0/49 – 52
ITKEAS01 (config-if)#ip dhcp snooping trust
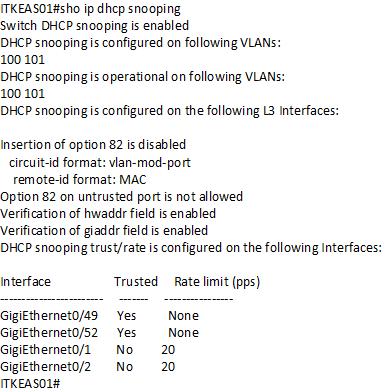
Finally we are going to configure VLANS for DHCP snooping DHCP snooping will used on all the VLANs (VLAN 100 & 101)except management VLAN 50 . Also we will limit the requests rate received in the Access Switch (ITKEAS01) ALL SWITCHES(config)# ip dhcp snooping VLAN 100,101
ITKEAS01(config)#interface range gigabitEthernet 0/1 – 48
ITKEAS01 (config-if)#ip dhcp snooping limit rate 20
Displaying the DHCP snooping
For further reference please do check this article from Cisco about DHCP snooping.
—Original Reading from itknowledgeexchange.techtarget.com
More Related Cisco Network Tips
How to Configure DHCP Snooping?
How to Configure DHCP on a Cisco Router or Cisco Switch?