“What is your favorite use of the word Virtual? Virtual Machine, Virtual Reality, Virtual Assistant? One of my favorites is Virtual Local Area Network, (VLAN). Join me as we discover the secrets of the VLAN and why it is a critical tool in today’s networks.”
Here Keith Barker wrote an article ‘What Happens in the VLAN Stays in the VLAN’ to share his opinions and thoughts of role of VLAN, more details as follows
How well do You Deal with Interruptions?
Imagine going to a conference where there were four sessions (1 through 4) being presented. A single large ballroom was rented at a nice hotel for the event, and a session was being presented in each corner of the ballroom. Listeners could hear each of the presenters in their respective corner, but there’s a problem. Frequently, over the broadcast system that can be heard by the entire room, announcements are periodically being made. Every time an announcement is made, everyone in all the sessions to stop what they were doing to see if the message being broadcast was important or relevant to them. If the broadcast message wasn’t relevant to an individual, they turn their attention back to their session. If the broadcast was relevant to an individual, such as “Would Bob Jones identify yourself, we have found your wallet.”, then Bob would respond appropriately by raising his hand, (while everyone that wasn’t Bob will never get that time back).
Broadcasts that interrupt every host are a way of life in the Network.
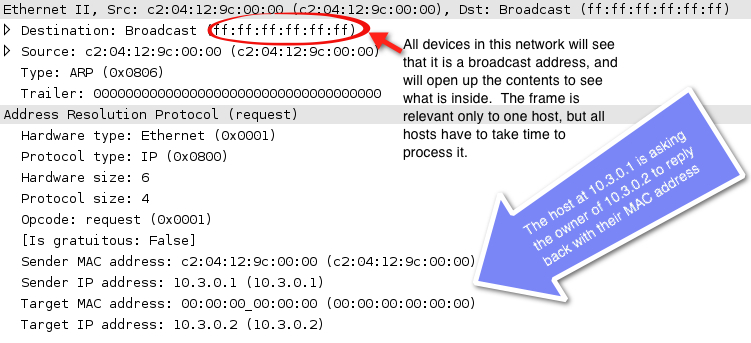
In an Ethernet network running IPv4, broadcasts are necessary interruptions that go to all devices in that same network/broadcast domain. Consider this packet in Figure 1.
This is an example of when a broadcast would be generated, namely, when a device is trying to learn the MAC address of another device on the local network. Because the sender doesn’t know what the Layer 2 MAC address is yet, a broadcast is sent, which all other devices must process to see if the message being carried is relevant to them. Then the device that has the MAC address being looked for (in our example, the host of 10.3.0.2) will respond with a reply, while all the other devices on the network go back to their normal business.
The level of tolerance
A small network with a few dozen hosts won’t normally generate a large amount of broadcasts, so the interruptions to the group are acceptable. But as we add more devices to that same network, such as a thousand new hosts, the quantity of broadcasts (which interrupt all other hosts on that same network) becomes high enough to bog down all the devices on that network. Imagine being interrupted hundreds of times per hour, or even per minute, and you get the picture of what the hosts on that network are going through. We do have some options for reducing the number of broadcasts that each of our hosts has to process. Read on and we will take a look together at a solution.
Reducing the Impact of Broadcasts
A solution to the problem of having too many devices (and as a result too many broadcasts) on a single network (which is a single broadcast domain) is to take a large network of 1000 hosts and carve it up into smaller networks, (for example, four networks of 250 hosts each). Let’s call these smaller networks 1, 2, 3, and 4. Each of these four smaller networks would be a separate broadcast domain. If a broadcast was generated in network 1, it would only have to be processed by devices in that same network. The other networks would only have to process the local broadcasts in their own smaller network. Broadcasts that begin in a broadcast domain/network, stay in that same broadcast domain/network.
Carving out the smaller networks
Let’s visualize a Layer 2 switch that has 1000 ports (and yes, I know, that is a lot!) If we connected computers to most of those ports, by default we would have one large network (one large broadcast domain), and too many broadcasts, as discussed earlier. To create the smaller networks, we could purchase 3 additional switches, and move 250 devices to each of the switches, or we could train the original 1000 port switch to logically create the 4 separate networks. Perhaps we tell the switch that ports 1-250 belong to network 1, ports 251-500 belong to network 2, ports 501-750 belong to network 3, and ports 751-1000 belong to network 4. These would be four separate broadcast domains, disconnected from each other. There is a feature that allows this, called a Virtual Local Area Network, which is really just an individual broadcast domain.
VLANs to the Rescue
A Virtual Local Area Network (VLAN) is the function in the switch that can separate one or more ports and put them in their own broadcast domain. VLAN is synonymous with “broadcast domain.” From our example earlier, if we assign ports 1-250 to VLAN 1, ports 251-500 to VLAN 2, ports 501-750 to VLAN 3, and ports 751-1000 to VLAN 4, then any devices we connected to those switch ports would belong to the VLAN that the specific switch port is assigned to. Now a single broadcast sent into any of the networks would be confined to that domain, or in other words be limited to only the other devices in that same VLAN. From our title, “What happens in the VLAN (related to L2 broadcasts) stay in the VLAN.”
Table 1
Ports on the Switch | VLAN assignment of those switch ports |
FastEthernet 1-250 | VLAN 1 |
FastEthernet 251-500 | VLAN 2 |
FastEthernet 501-750 | VLAN 3 |
FastEthernet 751-1000 | VLAN 3 |
The role of IP addresses
The VLAN are like streets that are man-made with heavy machinery. Imagine four separate streets that have just been leveled and paved with asphalt. The only problem with these new streets is that they haven’t been named. They will be given names as we place houses on those streets, and each house will have the common street name, as well as a house number. In our networks, each VLAN is simply an un-named (from an IP perspective), separate Level 2 broadcast domain, until we add the first IP device(s) or hosts to that VLAN.
As an example, let’s suppose we connect two PCs to ports 1 and 2 of the switch so that each host is associated with VLAN 1 (due to the configured switch ports the PCs are connected to). The PCs, even though they are in the same broadcast domain (VLAN), must also be configured to be on the same logical IP network, which is configured on each PC. If both PCs were configured to be on the 23.1.2.0/24 network, with a full IP address of 23.1.2.10/24 and 23.1.2.11/24 respectively, they would then be able to communicate with each other using IP. We could add a router that has an interface connected to a switch port that is in the same VLAN, and give the router an IP address of 23.1.2.1/24 and then tell the PC’s to use the router as a default gateway if they ever wanted to communicate with devices on a different network than the local 23.1.2.0/24. The router, to be effective, would need three more interfaces, each connected to the other three VLANs, (for example, switch ports 251, 501 and 751), and would need compatible IP addresses for those other three networks that agreed with the other devices in each of those VLANs. There is usually a correlation of one IP network or sub network with one VLAN.
Cisco CCNA Book Recommended:
CCNA 640-802 Official Cert Library, Updated, 3rd Edition
New Edition of Best Selling Official Cert Guide: Updated Content, New Exercises, and Expanded Coverage — PLUS includes CCNA Network Simulator Lite Edition with 21 free CCNA Network Simulator Labs
The new edition of bestselling CCNA 640-802 Cert Library, Updated Third Edition by Wendell Odom is a comprehensive review and practice package for the latest CCNA exams. The two books contained in this package, CCENT/CCNA ICND1 640-822 Official Cert Guide, Third Edition, and CCNA ICND2 640-816 Official Cert Guide, Third Edition, present complete reviews and a more challenging and realistic preparation experience. The books have been refreshed to provide updated coverage of critical exam topics such as IP addressing, subnetting, TCP/IP and OSI networking models, VLSM, route summarization, and IP access control lists.
More Details and REVIEWS of CCNA 640-802 Official Cert Library, Updated, 3rd Edition you can see at CiscoPress.com
Note: Keith Barker is a network technician for Electronic Data Systems (EDS) in 1985, and has had experience in IT and networking for over 25 years. Keith holds Cisco CCIE certifications in both security and routing/switching, CCDP and is a Cisco Certified Systems Instructor (CCSI). Keith also holds a CISSP certification.
More Cisco and Network Tips:
LAN and Setup VLAN on a Cisco Switch
How to Configure InterVLAN Routing On Layer 3 Switches?
How to Setup VLAN Trunking Protocol (VTP) on Cisco Switches?