In the intricate world of enterprise networking, understanding the fundamental differences between Port 80 and Port 443 is not just technical trivia; it’s a cornerstone of secure, efficient, and compliant data communication. For network engineers and IT decision-makers, distinguishing between these two critical ports directly impacts application performance, data protection, and strategic network design. As cyber threats evolve and data privacy becomes a global imperative, a deep dive into Port 80 vs 443 becomes indispensable for safeguarding organizational assets and ensuring a robust digital infrastructure.
Part 1: Technical Breakdown: HTTP vs. HTTPS and Their Default Ports
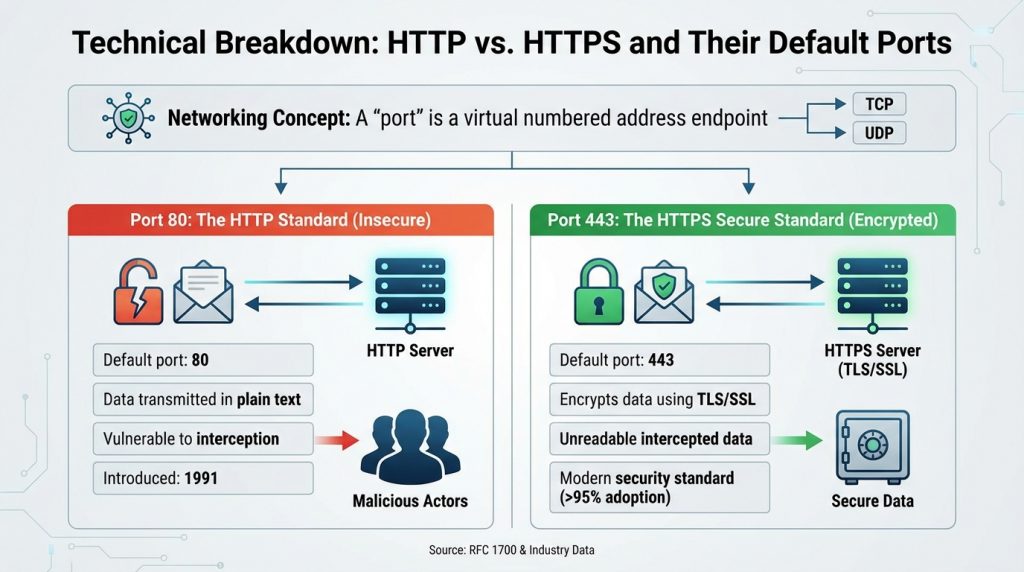
A “port” in computer networking is a virtual numbered address acting as an endpoint for communication, associated with Transport Layer Protocols like TCP and UDP. Both Port 80 and Port 443 are primarily associated with TCP, used where data reliability and security are crucial.
Port 80: The HTTP Standard
Port 80 is the default port for HTTP (Hypertext Transfer Protocol), introduced in 1991. HTTP enables users to connect to web pages but transmits data in plain text, leaving information vulnerable to interception by malicious actors.
Port 443: The HTTPS Secure Standard
Port 443 is the default port for HTTPS (Hypertext Transfer Protocol Secure), a secure version of HTTP using TLS/SSL encryption (published in RFC 1700). HTTPS encrypts data, ensuring that even if intercepted, it remains unreadable without the correct key. Over 95% of accessed websites now use HTTPS, reinforcing it as the modern security standard.
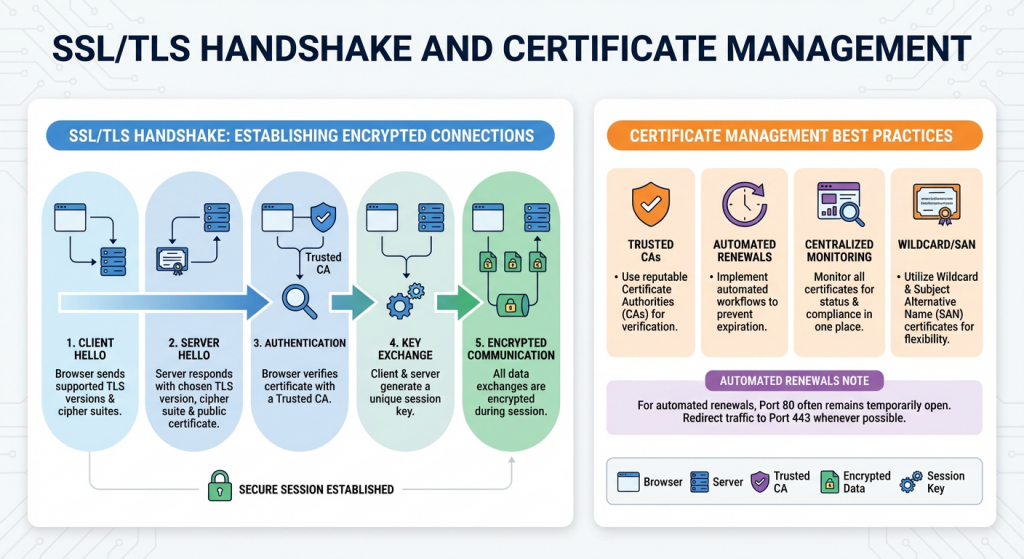
Part 2:SSL/TLS Handshake and Certificate Management
SSL/TLS certificates establish encrypted connections by verifying server identity and facilitating secure key exchange:
- Client Hello: Browser specifies supported TLS versions and cipher suites.
- Server Hello: Server responds with chosen TLS version, cipher suite, and its public certificate.
- Authentication: Browser verifies the certificate with a trusted CA.
- Key Exchange: Client and server generate a unique session key.
- Encrypted Communication: All data exchanges are encrypted during the session.
Certificate management best practices include using trusted CAs, automated renewal workflows, centralized monitoring, and wildcard/SAN certificates. For automated renewals, Port 80 often remains temporarily open, but redirect traffic to Port 443 whenever possible.
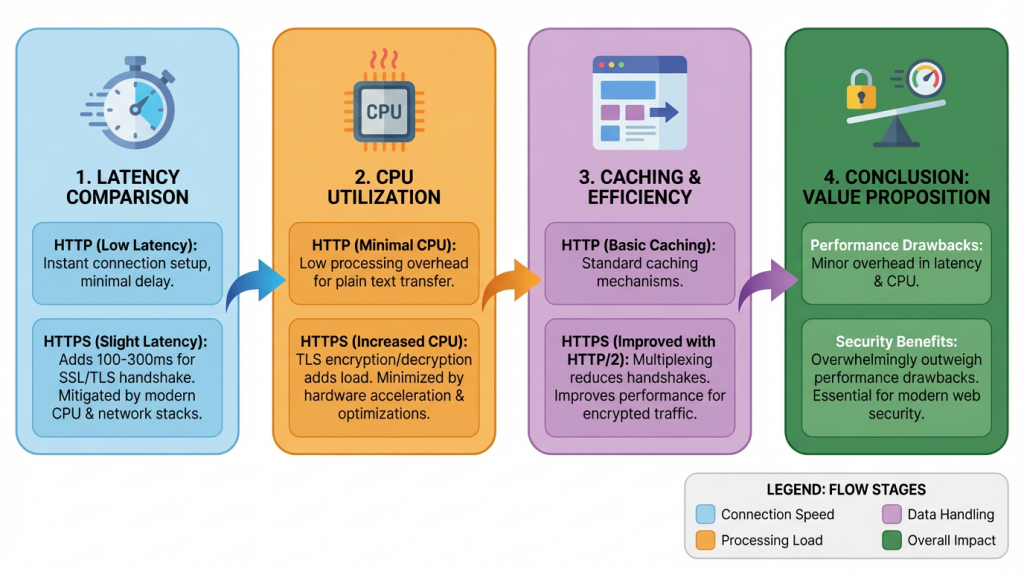
Part 3:Performance: HTTP vs. HTTPS
Latency
HTTPS introduces slight latency during the SSL/TLS handshake, adding around 100–300ms, but modern CPU and network stacks mitigate this impact.
CPU Utilization
TLS encryption and decryption increase CPU usage on servers, especially for high-traffic applications. Hardware acceleration and TLS optimizations minimize performance concerns.
Caching
Using HTTP/2 with HTTPS allows multiplexing requests over a single connection, reducing repeated handshakes and improving performance for encrypted traffic.
Despite minor overhead, the security benefits of HTTPS overwhelmingly outweigh performance drawbacks.
Part 4:Security: HTTP vs. HTTPS
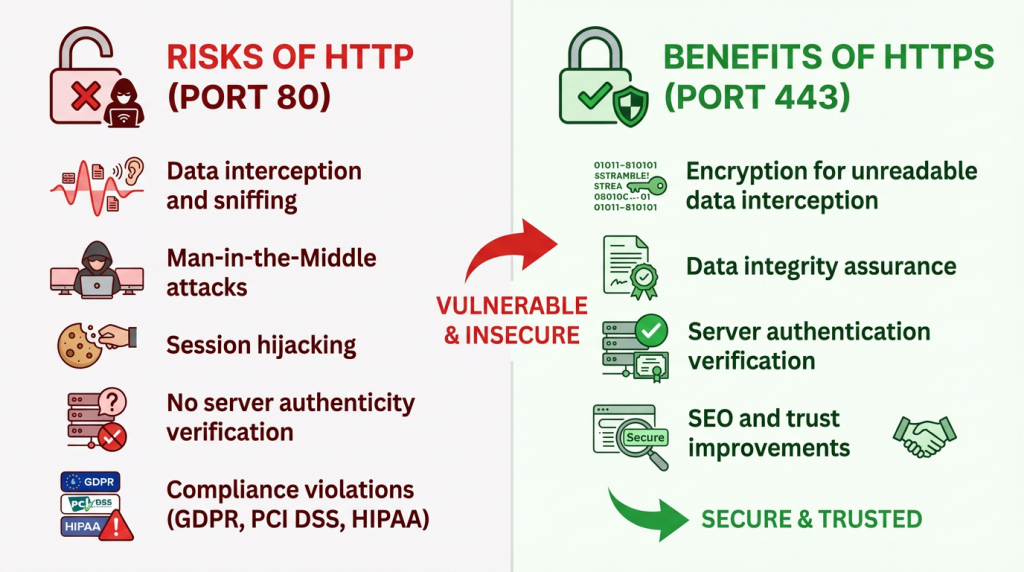
Risks of HTTP (Port 80)
- Data interception and sniffing
- Man-in-the-Middle attacks
- Session hijacking
- No server authenticity verification
- Compliance violations (GDPR, PCI DSS, HIPAA)
Benefits of HTTPS (Port 443)
- Encryption for unreadable data interception
- Data integrity assurance
- Server authentication verification
- SEO and trust improvements
Part 5:Enterprise Deployment Recommendations
Force HTTPS using server-side redirects and HSTS to enforce HTTPS:
server {
listen 80;
server_name yourdomain.com www.yourdomain.com;
return 301 https://$host$request_uri;
}Use SSL VPN devices for remote access instead of exposing internal services. Explore our SSL VPN devices for secure remote access.
Implement reverse proxies, harden servers, and segment networks using Cisco and Aruba switches with VLANs and Next-Generation Firewalls to control traffic and reduce exposure.
Part 6:People Also Ask (FAQs)
Q1: Are port 80 and 443 the same?
No, Port 80 is for HTTP (unencrypted), while Port 443 is for HTTPS (encrypted).
Q2: Can port 80 be used for HTTPS?
Technically possible but highly unconventional. Standard HTTPS traffic uses Port 443.
Q3: What is port 80 used for?
For HTTP-based traffic, now largely replaced by HTTPS due to security concerns.
Q4: Is port 80 the same as 8080?
No, Port 8080 is a common alternative for HTTP when Port 80 is in use, while Port 443 is used for HTTPS.
For a concise comparison and quick reference, visit our Port 80 vs 443 FAQ page.
To strengthen your enterprise’s secure connectivity, explore our Cisco Routers and Enterprise Switches for building scalable, secure foundations for HTTPS and secure services across your environment.
Conclusion
The evolution from Port 80 to Port 443 represents the internet’s pivot toward privacy, compliance, and trust. For enterprises, enforcing HTTPS and deploying layered security is essential to protect assets and customer data while maintaining compliance and trust.

Expertise Builds Trust
20+ Years • 200+ Countries • 21500+ Customers/Projects
CCIE · JNCIE · NSE7 · ACDX · HPE Master ASE · Dell Server/AI Expert