The PIX is a firewall appliance based on a hardened, specially built operating system, PIX OS, minimizing possible OS-specific security holes. The PIX has received ICSA Firewall and IPsec certification as well as Common Criteria EAL4 evaluation status.
PIX firewalls provide a wide range of security and networking services including:
- Network Address Translation (NAT) or Port Address Translation (PAT)
- content filtering (Java/ActiveX)
- URL filtering
- IPsec VPN
- support for leading X.509 PKI solutions
- DHCP client/server
- PPPoE support
- advanced security services for multimedia applications and protocols including Voice over IP (VoIP), H.323, SIP, Skinny and Microsoft NetMeeting
- AAA (RADIUS/TACACS+) integration
PIX can be graphically managed using the integrated Web-based management interface known as the PIX Device Manager (PDM) or by the Cisco Secure Policy Manager 2.3f and 3.0f (not to be confused with CSPM 2.3.3i which is for intrusion detection system management). The PDM is a PIX-specific device configuration and management tool whereas CSPM is generally used as part of a larger security management infrastructure and allows one to correlate organizational security policies with a PIX configuration. Management interfaces include command-line interface (CLI), telnet, Secure Shell (SSH 1.5), console port, SNMP, and syslog.
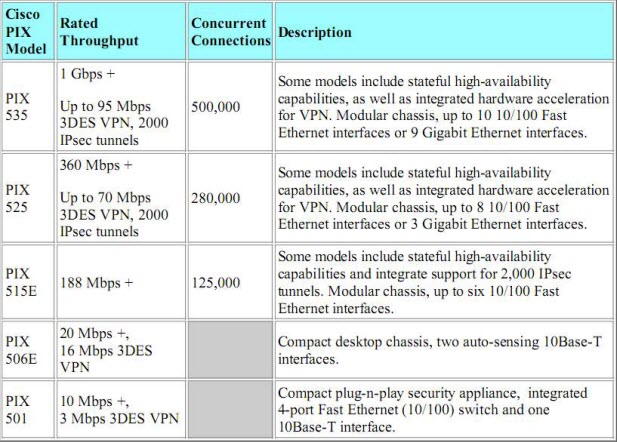
Cisco PIX Models
See https://www.cisco.com/warp/customer/cc/pd/fw/sqfw500/ for information about the PIX product line in general, or for more details or the latest models added to this product line.
PIX Terminology and Background Information
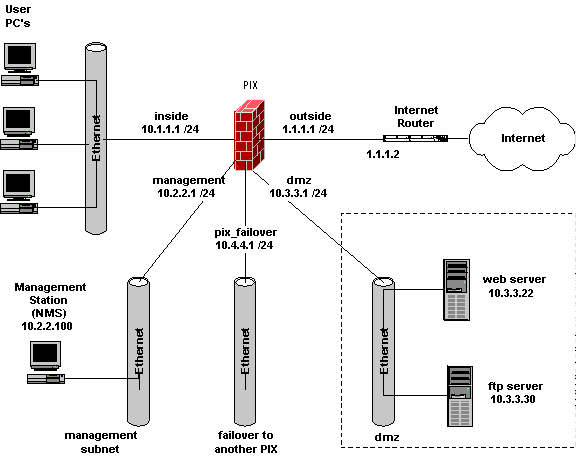
The following diagram shows a multi-port PIX connected to various networks. We will use this diagram as we build up a PIX configuration in this and any subsequent PIX articles.
PIX terminology: we generally refer to the user segment as the Inside subnet. The interface connected to the Internet router is the outside subnet. As shown, we probably have DMZ (De-Militarized Zone) subnet, the subnet where we quarantine all servers that are accessible from the outside. We might also have a separate management subnet and a subnet tying to a redundant PIX for failover (if supported/licensed).
The PIX Command-Line Interface (CLI) is somewhat like the Cisco IOS interface, but different. Use colon (“:”) for comments (which, as usual, are not retained). Newer PIX OS uses ACL’s, replacing the former conduits (which were arguably more confusing to experienced Cisco router administrators).
PIX interfaces are normally shutdown until the administrator activates them.
PIX interfaces have an associated security level. Two interfaces at same level can’t send packets to each other. We’ll shortly see that you set levels with nameif command. Connections and traffic are normally permitted from higher to lower security level interfaces, although you do have to put in some basic configuration to allow traffic to flow. Connections the other way (from low to high security) are disallowed unless the configuration explicitly permits them.
You actually do not have to put any ACL if going from a higher security level to a lower. Everything will be allowed. Best practice is to put an ACL on all interfaces even if the ACL permits everything to flow using “ip any any”. An ACL put inbound (PIX only does inbound ACLs) to the inside interface can control traffic destined going outbound. If an admin wants to only have www and dns traffic outbound he would allow only tcp on 80 and udp on 53 then everything else like real audio would be denied as it goes out.)
To let traffic flow from a high security level to a lower level, use the nat and global commands. For the opposite direction, from lower to higher, use the static and access-list commands. We suggest using nat and global when going from any non-outside interface to the outside interface (Internet usually unless the PIX is used as a border between business units) which is a little different than the first sentence above. We also suggest using statics from any non-outside interface to any other non-outside interface (like inside to management or ethernet3 to ethernet4, below.)
The PIX normally uses stateful NAT connections and stateful security, referred to as the Adaptive Security Algorithm (ASA). The PIX does not pass multicast traffic. (Can you say “DVMRP tunnel”?)
Cisco and we recommend you do not dynamic routing to or through the PIX. The PIX does support RIP, but the authors both loathe RIP. And static routing is more secure, cannot be as easily fooled.
PIX Configuration
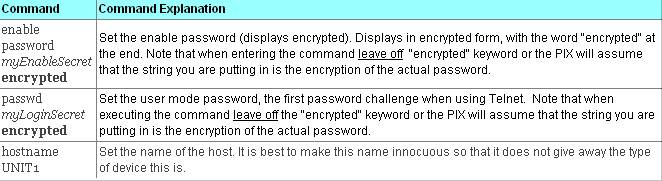
We’ll start off with good housekeeping. Enter configuration mode with “config t”. You’ll want to assign a hostname / prompt name so you can tell which device you’re on. You’ll also want to set up passwords.
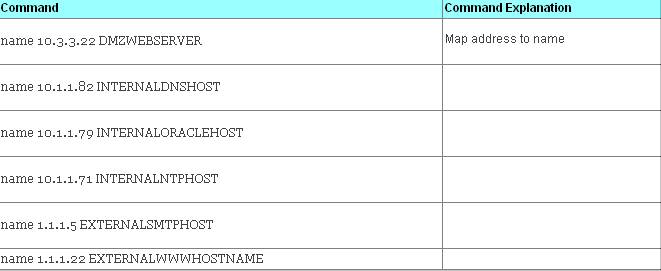
The PIX does allow you to set up a hosts table as a management convenience. Because there is no connection to DNS or /etc/hosts on UNIX servers, use of this command is a mixed blessing. It makes configurations much more readable but introduces another level of administration. Not only do you have to add and delete IP addresses to your configuration as you do now. But with this command, you also need to ensure that the host names match existing names.
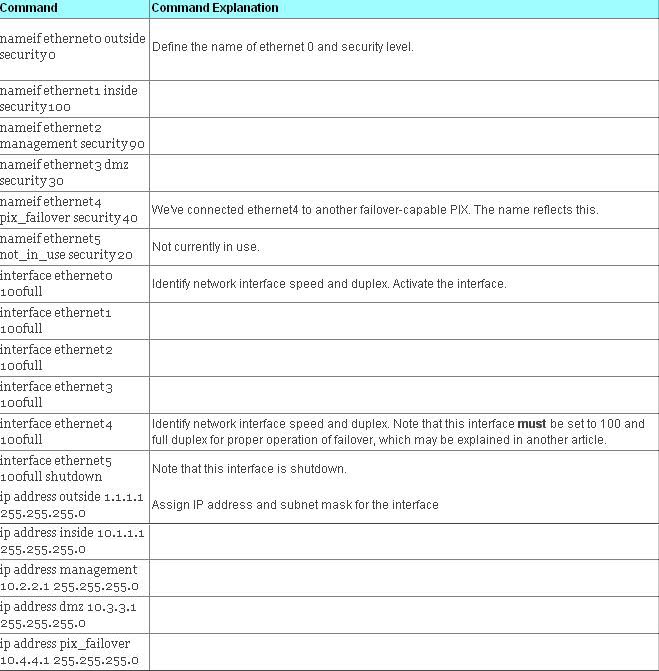
To start adjusting the default PIX configuration, one usually names the interfaces and assigns them security levels. (0 = least trusted; 100 = most trusted). We then specify the speed for each interface, carefully leaving off the default shut down keyword at the end to activate (enable) the interface. We do this for each interface we’re going to use. We have one extra unused interface which we shut
We also need to assign IP addresses to the interfaces that will be carrying IP traffic. One trick you can use on a shutdown interface is to assign it the loopback address, 127.0.0.1. This prevents accidental forwarding of traffic through that interface.
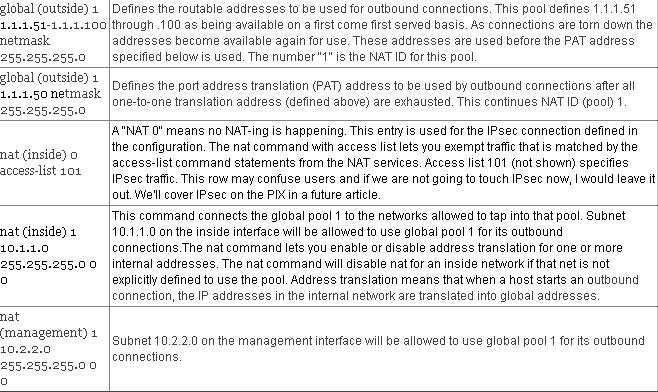
After the PIX has been addressed, we need to think about what it is to do with the addresses of other devices. Do we wish to use Network Address Translation (NAT)? Network Address Translation (NAT) lets your network have any IP addressing scheme and the firewall protects these addresses from visibility on the external network. If we have global Internet addressing and do not wish to re-address our computers, we can assign NAT ID 0 within the PIX to disable NAT. Let’s assume for our sample configuration that we do wish to perform NAT. (Looking at the above diagram, we have to do NAT, network 10.0.0.0 /8 is a private address range.
We generally put a global command on each lower security interface we want our internal users to have access to, although statics can be preferable for internal-internal access (see below). The main decision (other than addressing design) is whether to use one or multiple NAT ID’s. Using unique NAT ID’s limits access to specific interfaces. Using one NAT ID is simpler and assumes the PIX will sort out which nat command (below) pairs up with which global command on which interface.
We put nat commands on the higher security interfaces, allowing users to start connections to lower security level interfaces with global commands on them. The NAT ID ties the inside addresses in the nat command to the pool of addresses in one or more global commands with the same NAT ID.
Port Address Translation is where all inside addresses appear as one outside address, with shifted ports. PAT has some restrictions, for example it cannot support H.323 or caching nameserver use, so you may want to use it to augment a range of global addresses rather than using it as your sole global address.
Let’s see what that looks like:
Note that if acl 101 is undefined, no IPsec traffic will match and no traffic will go through the IPsec tunnel. All traffic would then be subjected to NAT.
If you’ve used NAT before, you’ll recognize that servers on the inside that need to be connected to from the outside will need static mappings. The static command creates a permanent mapping (called a static translation slot or “xlate”) between a local IP address and a global IP address. Use the static and access-list commands when you are accessing an interface of a higher security level from an interface of a lower security level. When NAT exists between two interfaces the command takes the form of “static (high,low) low high” . Without address translation, the format of the static command becomes different: “static (high,low) high high”.
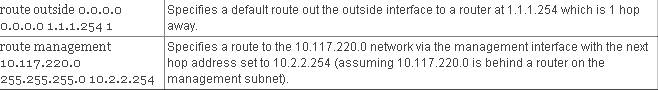
We also need some static routing, so the PIX knows which subnets are out which interface. Like Cisco routers, the PIX does know how to route to connected subnets, so you only have to specify subnets or address ranges behind other routers. You can only have one default route for the PIX Firewall.
TIP: If you use statics you will also be able to go from higher to lower without having to use nat and global. Example: suppose management station 10.2.2.2 (NMS) needs to talk to serv1 at 10.1.1.15 on the inside. Configure:
static (inside,management) 10.1.1.15 10.1.1.15 netmask 255.255.255.255
access-list from-management-coming-in permit tcp host 10.2.2.2 host 10.1.1.15 eq 8888
access-group from-management-coming-in in interface management
Because the static exists, 10.1.1.15 can also inititate connections to 10.2.2.2 but cannot talk to 10.2.2.50 (NMS2) because no method of translation exists.
Another example:
static (inside,management) 10.1.1.0 10.1.1.0 netmask 255.255.255.0
This allows each network to address the other. The inside can then talk to everything on the management net and reply packets are let back through by virtue of stateful inspection but an ACL must exist for the management net to initiate anything to the inside.
There are some other variations one can do, but statics are clearer and you can predict behavior because no timeouts for the connections exist and you still retain ultimate control via the ACL.
NOTE: Cisco PIX Firewall Doc
More Cisco Firewall Info:
Cisco Ramps up Its Firewall Options
Cisco ASA 5500 Family, Key Component of the Cisco Secure Borderless Network