“What’s the order in which IOS processes the running config between the following items?
ACL
Distrubute list,
Route map
Routing Protocol
Routing
What im looking for is the packet flow when it arrives thru an interface for better understanding?
Does it go to acl first then nat then routing logic then routing table…?
or
Is it something like…this is the running config…if something doesnt work check these areas: ACL Dist list Route map, Routing protocol routing table, etc, not necessarily in a particular order
What’s the way a CCIE thinks?”
—Q from the Cisco Learning Network
The Cisco IOS order of operations plays an important role in how a router processes traffic. The order of operations tells the router how to process traffic according to the configuration of different router features.
If you’re simply using the most basic features of the router, chances are good that you’ll never have to think about the order of operations. However, when configuring features such as Network Address Translation (NAT), Quality of Service (QoS), and encryption, it’s essential to understand the order of operations in order to configure these features successfully.
Using the Cisco IOS actually involves two different orders of operations tables: the NAT Order of Operations and the QoS Order of Operations. Let’s take a look at each.
NAT Order of Operations
Before you can understand the NAT Order of Operations list, you first need to understand NAT. In its most basic form, NAT translates one IP address to another IP address.
When the router uses this order of operations, it takes the inbound packet, starting at the top and moves down the list. If the packet is from a NAT inside-designated interface, it uses the inside-to-outside list. If the packet is from an outside-to-inside interface, it uses that list.
Here’s the order of operations for the inside-to-outside list:
- If IPSec, then check input access list
- Decryption—for Cisco Encryption Technology (CET) or IPSec
- Check input access list
- Check input rate limits
- Input accounting
- Policy routing
- Routing
- Redirect to Web cache
- NAT inside to outside (local to global translation)
- Crypto (check map and mark for encryption)
- Check output access list
- Inspect context-based access control (CBAC)
- TCP intercept
- Encryption
Here’s the order of operations for the outside-to-inside list:
- If IPSec, then check input access list
- Decryption—for CET or IPSec
- Check input access list
- Check input rate limits
- Input accounting
- NAT outside to inside (global to local translation)
- Policy routing
- Routing
- Redirect to Web cache
- Crypto (check map and mark for encryption)
- Check output access list
- Inspect CBAC
- TCP intercept
- Encryption
More details in a larger diagram
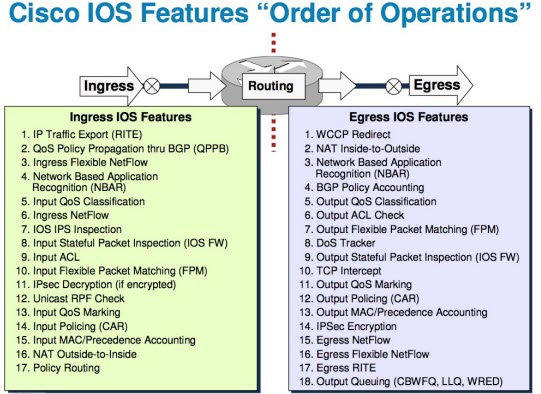
Let’s say that you have an IP packet coming in from an outside-to-inside interface. When translating that packet, you want to use an access control list to block traffic from certain IP addresses. Which IP address should you put in the ACL—the IP address before the packet’s translation (i.e., the public IP address), or the IP address after the packet’s translation (i.e., the private address)?
By checking the order of operations, you can determine that the “NAT outside to inside” operation occurs after the “Check input access list” task. Therefore, you would use the public IP address in the ACL because the packet hasn’t gone through NAT.
On the other hand, what if you want to create a static route for traffic going through NAT? Should you use the public (outside) or private (inside) IP address? In this case, you would use the private (inside) IP address because the traffic has already gone through NAT when it gets to the “Routing” operation.
QoS Order of Operations
The Quality of Service (QoS) order of operations is another important list to know. Of course, this is only really important if you’re using QoS. But if you are, you need to be familiar with it.
Here’s the order of operations for inbound traffic to the router:
- QoS Policy Propagation through Border Gateway Protocol (BGP)—or QPPB
- Input common classification
- Input ACLs
- Input marking—class-based marking or Committed Access Rate (CAR)
- Input policing—through a class-based policer or CAR
- IPSec
- Cisco Express Forwarding (CEF) or Fast Switching
Here’s the order of operations for outbound traffic from the router:
- CEF or Fast Switching
- Output common classification
- Output ACLs
- Output marking
- Output policing—through a class-based policer or CAR
- Queueing—Class-Based Weighted Fair Queueing (CBWFQ) and Low Latency Queueing (LLQ))—and Weighted Random Early Detection (WRED)
Being familiar with the order of operations is vital when it comes to understanding how the traffic within a router is flowing and how to control that traffic. In my experience, the NAT order of operations is most important when you’re using any combination of NAT, crypto, ACLs, routing, or other features on the list.
Without a proper understanding of the order of operations, you can spend an entire week troubleshooting a basic NAT and ACL combination—without any luck. Knowing about the order of operations can really make a difference.
Resource from techrepublic.com
More Related Cisco and Networking Tips:
How to Set up NAT Using the Cisco IOS?
How to Configure NAT in Cisco IOS?
How to Set Up PAT (Port Address Translation) in the Cisco IOS?