For almost all companies are connected to the Internet, the threat of network attacks is an inevitable problem that they need to face. So there is often a need to set up some type of intrusion detection system (IDS) or intrusion protection system (IPS). These systems’ main purpose is to detect attacks as they are being initiated; this detection is done by comparing the streams of incoming traffic against a database of known attacks.
The main differences between an IDS and an IPS is in what happens when the device detects an attack. An IDS will detect the attack and alert the network administrators/engineers; an IPS has the ability to directly block the attack traffic once it has been detected. This can proactively prevent a good amount of damage to the internal network.
Cisco ASA line adds this ability with an additional piece of hardware of software, depending on the base ASA model. In this article it will take a look at this additional capability, what it offers, and how it can be configured to monitor traffic through an ASA.
ASA IPS Module Details
The IPS module might be a physical module or a software module, depending on your ASA model.
The IPS module runs advanced IPS software that provides proactive, full-featured intrusion prevention services to stop malicious traffic, including worms and network viruses, before they can affect your network.
The exact details of the IPS functionalities of an ASA depend on the specific model of ASA that is being used. The ASA 5505, 5510, 5520, 5540, 5580, and 5585-X all use an additional hardware module that is inserted into the ASA chassis. The ASA 5512-X, 5515-X, 5525-X, 5545-X, and 5555-X all use an additional software module that is uploaded to the ASA.
The connection to manage the ASA module differs also by the model of the ASA used:
- ASA 5505: The ASA 5505 IPS module does not have an external management interface and is managed using a management VLAN within the ASA. By default, the VLAN that is used is 1, and the default IPS management IP address is 192.168.1.2.
- ASA 5510, ASA 5580, ASA 5585-X: These devices have an external management interface that is used to configure the device and the IPS module; the ASA 5585-X actually has several external management interfaces. With these devices, the ASA and the ASA IPS module are typically assigned with IP addresses that are on the same subnet (default: ASA – 192.168.1.1, ASA IPS – 192.168.1.2). It is also possible to configure the ASA to be managed via an inside interface while the ASA IPS module is solely managed via the external management interface.
- ASA 5512-X, ASA 5555-X: These devices work similarly to the previous models with an external management interface and with the same default IP addresses.
The Basic Operation of the ASA IPS Module
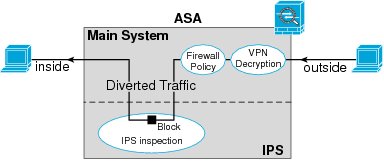
The basic ASA IPS module operation is simple: Traffic comes into the ASA and goes through the initial ASA processes (e.g., VPN decryption, firewall policy). Traffic that is matched is then sent to the IPS module; traffic that is allowed to pass is returned from the IPS module and can be sent back out another ASA interface.
The ASA IPS module does offer two different operating modes that can be specified within the traffic-matching configuration; these include inline mode and promiscuous mode. While in inline mode, all matched traffic will be sent to the ASA IPS module and will not continue on through the ASA until it is returned from the module.
While in promiscuous mode, a copy of the matched traffic is sent to the ASA IPS module with the initial copy of the traffic continuing through the ASA; if the ASA IPS module finds that specific traffic matches one of the attack signatures, it will send a shun message to the ASA to block any future traffic matching the specific traffic characteristics.
The choice of which operating mode to use depends on the specific implementation. Although the inline mode is more secure, it can also have some effect on traffic throughput. The promiscuous mode is the opposite: being less secure but not affecting traffic throughput. The promiscuous mode operates in a similar way to a traditional IDS, whose alerts can retroactively be used to block future traffic.
Virtual Sensors
All the ASA models except the 5505 support virtual sensors; these sensors are used when multiple contexts are used within the ASA. Each context can be configured with a virtual sensor, and the matching IPS policy can be configured with individual ASA IPS module settings.
ASA IPS Module Configuration
In an effort to keep this a little organized, the next few sections will split up the major sections of configuration.
ASA IPS Module Network Configuration
The first thing to cover is how to configure the basic network settings of the IPS module, assuming that the defaults are not acceptable. The way to do this differs between the ASA 5505 and all of the other models.
For the ASA 5505, the first thing to set up is the management VLAN. The process to configure these settings is shown in Table1:
Table1: ASA 5505 IPS Module Basic Network Settings
| 1 | Enter privileged EXEC mode. | asa>enable |
| 2 | Enter global configuration mode. | asa#configure terminal |
| 3 | Enter interface configuration mode (this is the current management VLAN interface). | asa(config)#interface vlan vlan |
| 4 | Disable IPS management. | asa(config-if)#no allow-sec-mgmt |
| 5 | Enter interface configuration mode (this is the new management VLAN interface). | asa(config-if)#interface vlan vlan |
| 6 | Enable IPS management. | asa(config-if)#allow-sec-mgmt |
| 7 | Exit Configuration mode. | asa(config-if)#end |
| 8 | Configure the ASA IPS module management IP address. Note: This IP address must be in the same subnet as the management VLAN interface configured in step 5. The gateway is the IP address of this same VLAN interface. | asa#hw-module module 1 ip ip_address netmask gateway |
| 9 | Configure the host(s) that are allowed to access the ASA IPS Module management address. | asa#hw-module module 1 allow-ip ip-address netmask |
For all other ASA modules, the first step is to session into the ASA IPS module. For the models using a software IPS module, there are two different methods to do this, as shown in Table2:
Table2: ASA IPS Module Session Methods (ASA 5510+)
| 1 | To access the ASA IPS module via telnet, for hardware IPS modules | asa#session 1 |
| OR | ||
| 1 | To access the ASA IPS module via telnet, for software IPS modules. | asa#session ips |
| OR | ||
| 1 | To access the ASA IPS module via console, for software IPS modules. | asa#session ips console |
NOTE: The specific configuration of the ASA IPS module is beyond the scope of this article, but from a Cisco documentation perspective, these modules are treated similarly to a Cisco IPS 4200 Series Sensor and their specific policy configuration is covered in the same documentation. For the specifics, check out https://www.cisco.com/en/US/products/hw/vpndevc/ps4077/products_documentation_roadmaps_list.html.
Virtual Sensor Configuration
When using the ASA IPS module with multiple contexts the use of virtual sensors can be very useful, this section will review the basic command that is used within each contexts system execution space. The name that is given to the virtual sensor within this section can then be used within the configuration shown in the next section.
To configure a virtual sensor, there is only a single command that is used within each context (see Table3).
Table3: Configuring ASA IPS Module Virtual Sensors
| 1 | Enter privileged EXEC mode. | asa>enable |
| 2 | Enter global configuration mode. | asa#configure terminal |
| 3 | Enter the specific context execution space. | asa(config)#context context-name |
| 4 | Assign a virtual sensor to the context. | asa(config-ctx)#allocate-ips sensor-name[mapped_name] [default] |
ASA IPS Module Policy Configuration
For the ASA to know which traffic to forward to the IPS module, there needs to be a policy configured. All the specific options for matching traffic will not be covered in this article, but the basic commands will be shown for clarity. Table 4 will review the steps needed to create an ASA IPS module policy.
Table4: Configuring ASA IPS Module Policy
| 1 | Enter privileged EXEC mode. | asa>enable |
| 2 | Enter global configuration mode. | asa#configure terminal |
| 3 | Create a class map. | asa(config)#class-map class-name |
| 4 | Specify a traffic match statement (or statements) Note: there are a number of differentmatch statement possibilities. | asa(config-cmap)#match parameter |
| 5 | Create a policy map. | asa(config-cmap)#policy-map policy-name |
| 6 | Link the previously created class map with the policy. Note: Multiple class maps can be linked to the same policy map. | asa(config-pmap)#class class-name |
| 7 | Configure the traffic that has been match to be sent to the ASA IPS module. Note: When the ASA is configured tofail-close, all traffic will be dropped if the ASA IPS module is unable to be contacted. | asa(config-pmap-c)#ips {inline |promiscuous} {fail-close | fail-open} [sensor {sensor_name | mapped_name} |
| 8 | Exit back into global configuration mode. | asa(config-pmap-c)#exit asa(config-pmap)#exit |
| 9 | Activate the policy my applying it globally or to a specific ASA interface (by name). | asa(config)#service-policy policy-name{global | interface interface-name} |
The ASA IPS module opens up the possibility of using a single appliance to do a number of things. However, there are downsides to its add-on functionality. All traffic that is configured in the inline operational mode is limited to the overall throughput possible with the specific ASA IPS module (it differs considerable by which model and module). In very high-bandwidth applications, IPS-only appliances are also offered by Cisco.
Hopefully the content of this article has provided you with at least a little better understanding of the capabilities of this solution and how it can be configured to increase the security of an organization’s (small to large) network.
Reference from https://www.ciscopress.com/
More Cisco ASA Topics:
How to Configure New ASA 5510 in Transparent Mode?
Cisco Security Advisory: Multiple Vulnerabilities in Cisco ASA Software
Cisco ASA CX–Next Generation Firewall or Enterprise Firewall?